Configuring OVOC Web Azure Settings - Multitenant Setup
This section describes how to configure Azure authentication in the OVOC Web interface for multitenant deployments. When operators login to OVOC, they're assigned with an OVOC security level, i.e. Admin, Operator or Monitor' based on their assigned role on Azure and their Tenant ID which reflects their tier permissions i.e. Tenant, Channel or Customer operator permissions. These details are sent to OVOC Azure via the Token authentication mechanism.
| ➢ | To configure authentication of OVOC operators using Azure AD: |
| 1. | In the OVOC Web, open the Authentication page (System > Administration > Security > Authentication), and then from the 'Authentication Type' drop-down, select AZURE. |
Azure Authentication
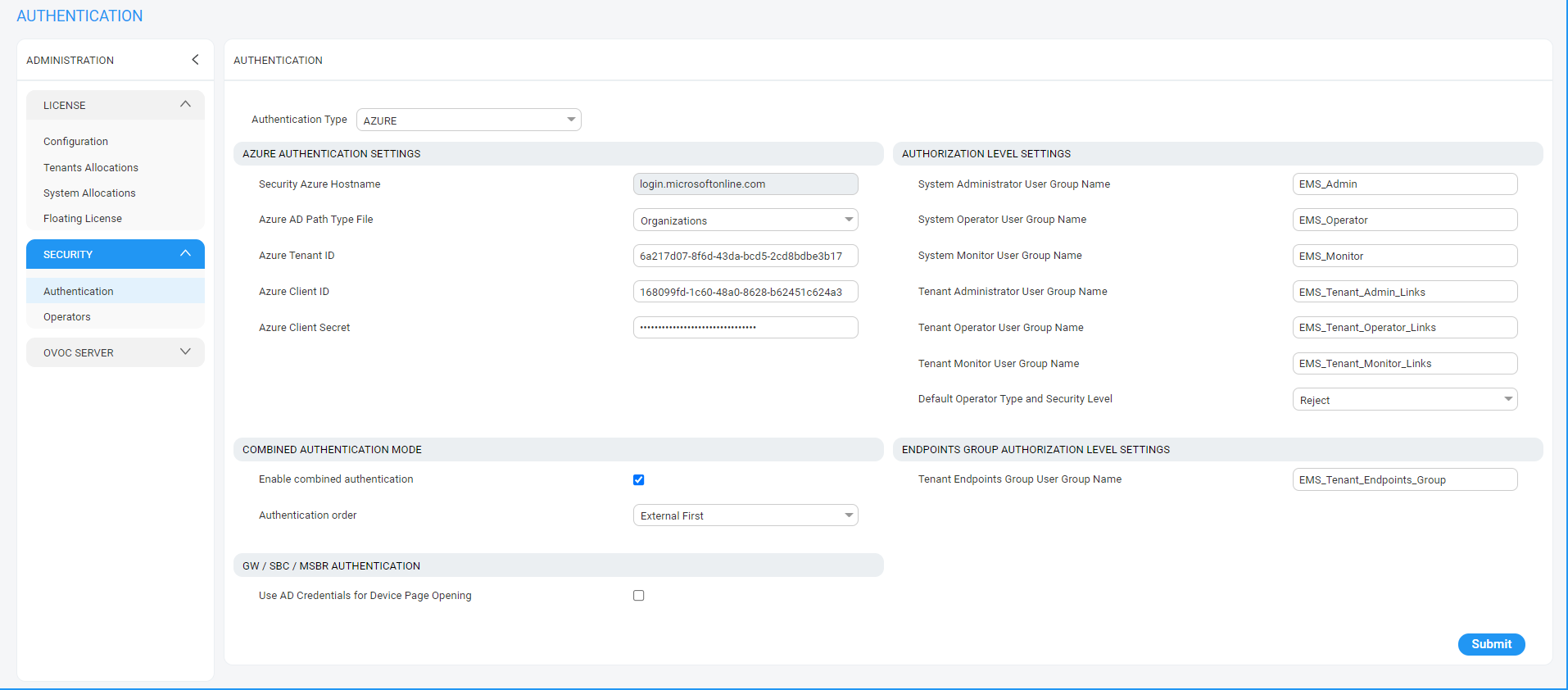
| 2. | From the 'Azure AD Path Type File' drop-down, select Organizations (default). OVOC can access Azure AD in the enterprise network if a standard service is purchased. |
| 3. | In the 'Azure Tenant ID' field, enter the Tenant ID of the Main Tenant. |
| 4. | In the 'Azure Client ID' field, enter the ID of the Azure AD client of the Main Tenant. |
| 5. | In the 'Azure Client Secret' field, enter the client secret of the Main Tenant. |
| 6. | In the screen section 'GW / SBC / MSBR Authentication', select the option 'Use AD Credentials for Device Page Opening' for the OVOC to sign operators in to AudioCodes devices using the same credentials they used to sign in to OVOC. The AudioCodes device will then perform authentication with the Azure AD and login to the device is attempted with same AD username / password instead of the local device user name / password. Note that the device must also be configured to authenticate with the same AD. |
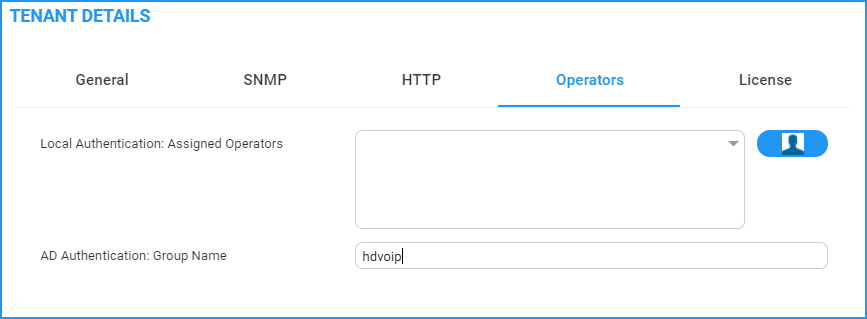
When a Main Tenant operator attempts to connect to OVOC, OVOC verifies the mapped Azure User Group to which the operator is a member.
| ● | In the Tenant Details screen under the Operators tab, the parameter AD Authentication: Group Name points to the Azure group which includes the Main Tenant operators who are authorized to login to OVOC using this method. |
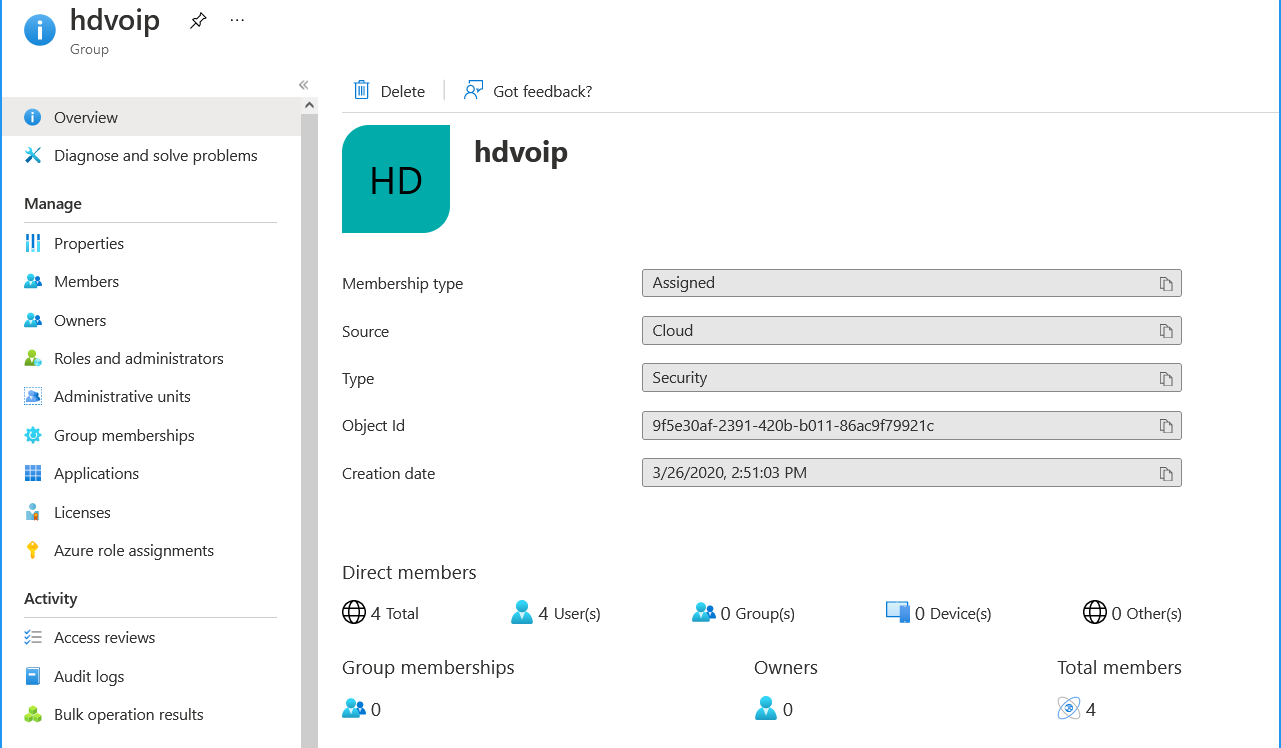
| ● | If the Azure AD successfully validates that the operator belongs to the AD Authentication group (see highlighted group in the example below), its and allowed access. |
AD Authentication Group Name
Matching Group on Azure
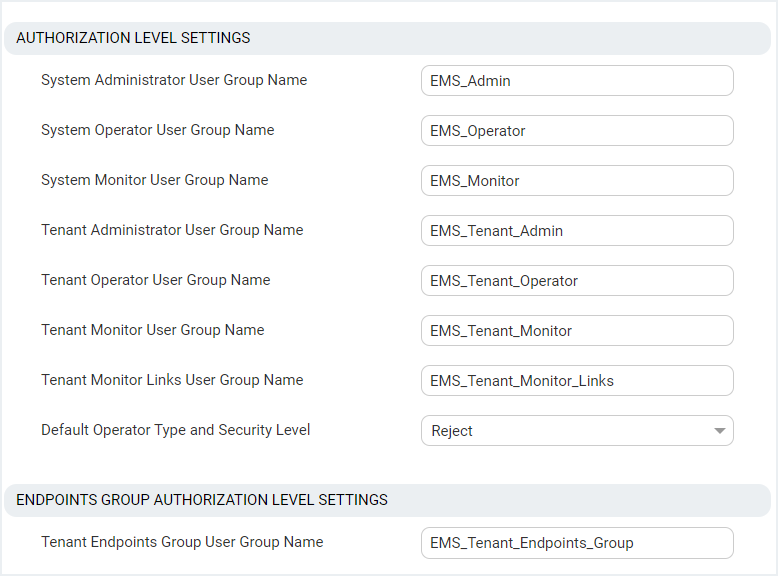
| 7. | In the screen section Authorization Level Settings, configure the user group names exactly as defined on Azure in Create Azure Groups and Assign Members. When an operator is not assigned to a group on Azure, the parameter 'Default Operator Type and Security Level' is applied. |
Authorization Level Settings
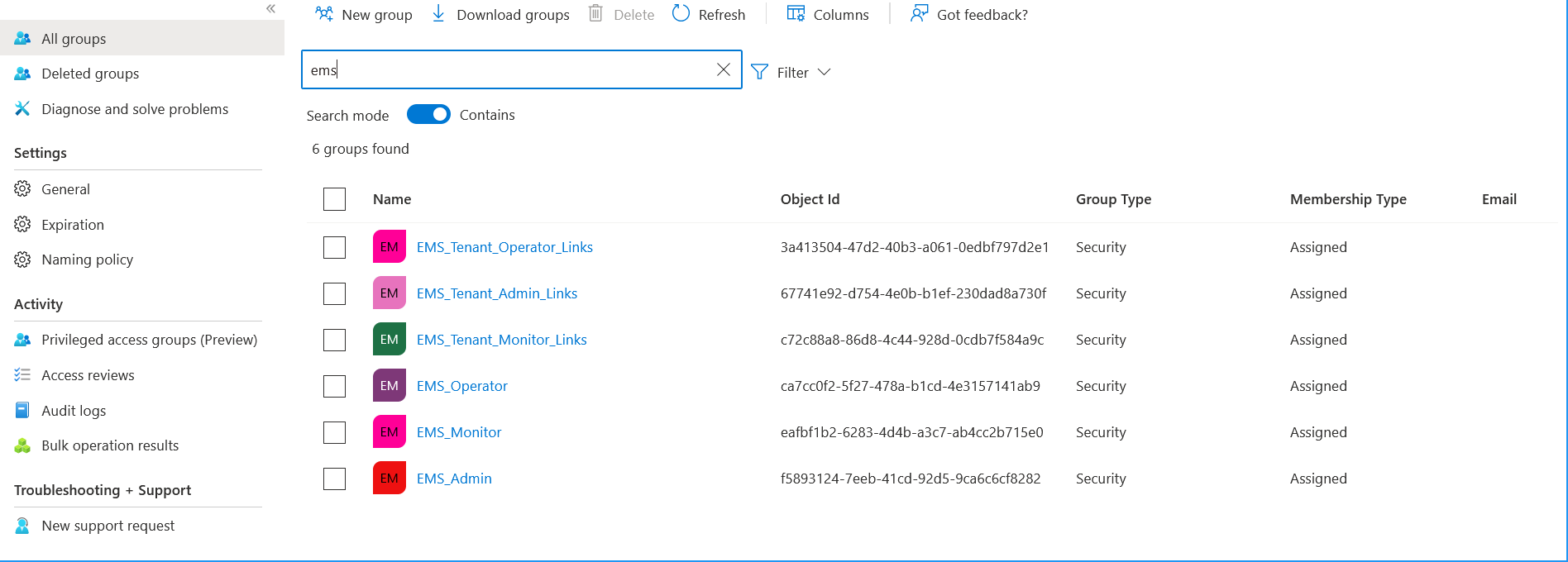
Matching Groups on Azure
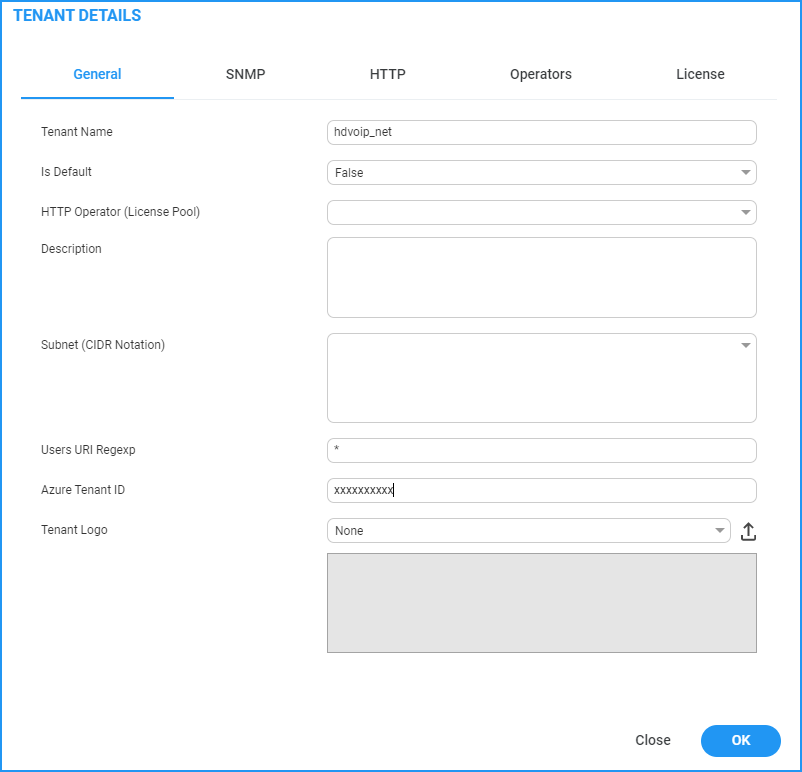
| 8. | In the Tenant Details, enter the "Azure Tenant ID" of the external managed tenant as shown in the screen below. |
Tenant Details
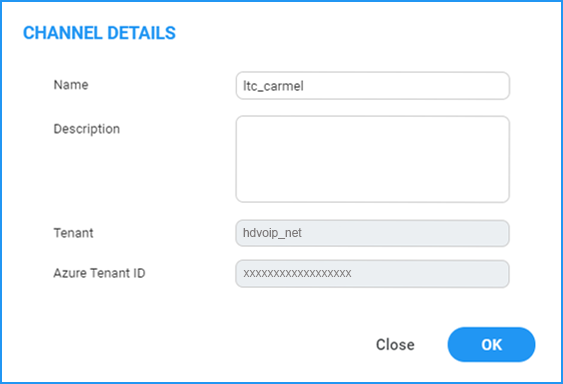
| 9. | If you are managing channels, in the Channels Details, enter the "Azure Tenant ID" of the external managed tenant as shown in the screen below |
Channel Details